
Northeast Data will ensure that it reacts appropriately to any actual or suspected incidents relating to information systems and information within the custody of Northeast Data.
The aim of this policy is to ensure that Northeast Data reacts appropriately to any actual or suspected security incidents relating to information systems and data.
This document applies to all Northeast Data departments, partners, employees, and customers, including but not limited to third parties who use Northeast Data IT staff and equipment or have access to, or custody of, customer information or Northeast Data Information.
All users must understand and adopt the use of this policy. We are all responsible for ensuring the safety and securityof Northeast Data’s systems and the information that they use or manipulate.
All users have a role to play and a contribution to make to the safe and secure use of technology and the information that it holds.
This policy needs to be applied as soon as information systems or data are suspected to be or are affected by an adverse event which is likely to lead to a security incident.
The definition of an “Information Management Security Incident” (‘Information Security Incident’ in the remainder of this policy and procedure) is an adverse event that has caused or has the potential to cause damage to an organizations asset, reputation and / or personnel. Incident management is concerned with intrusion, compromise and misuse of information and information resources, and the continuity of critical information systems and processes.
An Information Security Incident includes, but is not restricted to, the following:
Northeast Data recognizes that there are risks associated with users accessing and handling information to conduct official Northeast Data business. This policy aims to mitigate the following risks.
Noncompliance with this policy could have significant effect on the efficient operation of Northeast Data and may result in financial loss and the inability to provide necessary services to our customers.
Events and weaknesses are to be reported at the earliest possible stage as they need to be assessed by a Northeast Data Manager. The Manager enables the Human Resources Department to identify when a series of events or weaknesses have escalated to become an incident. It is vital for the Human Resources Department to gain as much information as possible from the business users to identify if an incident is occurring.
If any user is found to have breached this policy, they may be subject to Northeast Data’s disciplinary procedure.If a criminal offense is considered to have been committed, further action may be taken to assist in the prosecution of the offender(s).
For clarification of this policy or how it may apply to you, seek advice from Human Resources.
The following table identifies who within Northeast Data is Accountable, Responsible, Informed or Consulted with regards to this policy. The following definitions apply:
| Type | Name |
|---|---|
| Responsible | Christine Traver, Vice President Kimberly Wehler, Human Resources |
| Consulted | Lee Canfield, General Manager Matt Cokely, Installation Manager Troy Fitzgerald, Network Manager |
| Informed | Operations Department Installation Department Design Department Network Services Department Network Integration Department |
This policy will be reviewed as it is deemed appropriate, but no less frequently than every 12- months.
Policy review will be undertaken by the Human Resources Department.
The following Northeast Data policy documents are directly relevant to this policy
All Staff should report any incidents or suspected incidents immediately by contacting their direct supervisor.
Northeast Data will maintain your anonymity when reporting an incident.
If you are unsure of anything in this policy, you should ask for advice from the HR department.
For Activity Process follow blue for documentation follow yellow
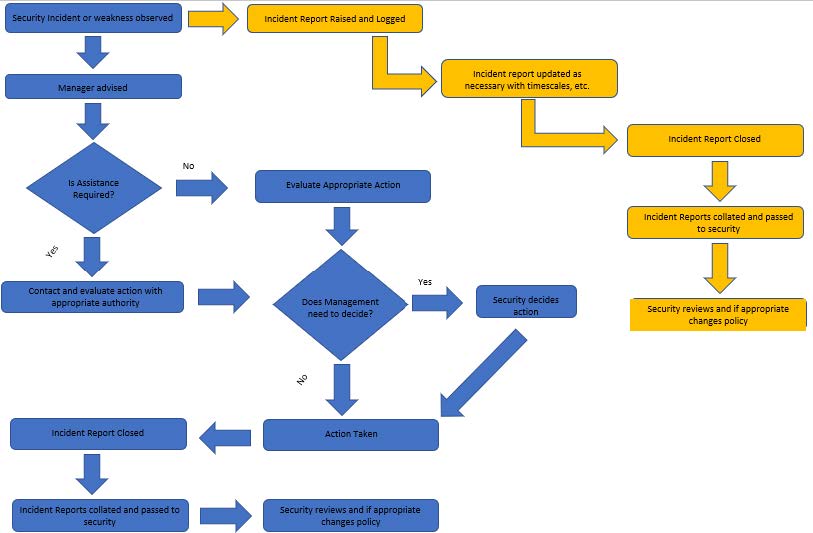
The below list shows examples of Security Incidents and may not contain every situation
For activity reporting and investigations:
Report the incident to your Manager. The manager will then advise HR. The action will be evaluated by the Management team. Appropriate action will be taken based on the security incident. A copy of the incident will be placed in the employee file. Appropriate personnel will be notified if this is a customer or a Northeast Data incident.
For Documentation reporting :
After the incident is reported to the manager, the incident will be recorded and logged including updating the incident information with timescales. The policy will be reviewed and adjusted as necessary.
Security events, for example a virus infection, could quickly spread and cause data loss across the organization. All users must understand and be able to identify that any unexpected or unusual behavior on the workstation could potentially be a software malfunction. If an event is detected users must:
All suspected security events should be reported immediately to the Information Services Helpdesk at 570-996-6666.
If the information security event is in relation to paper or hard copy information, for example personal information files that may have been stolen from a filing cabinet, this must be reported to Senior Management and Human Resources for the impact to be addressed.
The information services helpdesk will require you to supply further information, the nature of which will depend upon the nature of the incident. However, the following information must be supplied.
Security weaknesses, for example a software malfunction, must be reported through the same process as security events. Users must not attempt to prove a security weakness as such an action maybe considered to be misuse.
Weaknesses reported to application and service providers by employees must also be reported internally to Information Services. The service provider’s response must be monitored and the effectiveness of its action to repair the weakness must be recorded by Information Services.
Information security events and weaknesses must be reported to a nominated central point of contact within Information Services as quickly as possible and the incident response and escalation procedure must be followed.
Security events can include but not limited to:
Security Weaknesses can include but not limited to:
The reporting procedures must be quick and have redundancy built in. All events must be reported to at least two nominated people within Information Services who both are required to take appropriate action. The reporting procedure must be clearly outlined, depicting the steps that are to be taken and the time frames that must be met.
An escalation procedure must be incorporated into the response process so that the users and support staff are aware who else to report the event to if there is not an appropriate response within a defined period.
Incidents must be reported to the Business Continuity Management team should the incident become service affecting.
An Incident Register must be maintained to capture relevant security incident details such as Incident detail. These details must include:
A consistent approach to dealing with all security events must be maintained across Northeast Data. The events must be analyzed, and the Security Advisor must be consulted to establish when security events become escalated to an incident. The incident response procedure must be a seamless continuation of the event reporting process and must include contingency plans to advise Northeast Data on continuing operation during the incident.
All high, medium, and low incidents should be reported to Human Resources.
If an incident may require information to be collected for an investigation, strict rules must be adhered too. The collection of evidence for a potential investigation must be approached with care. An Internal Audit must be completed, and Human Resources must be contacted for guidance and strict processes must be followed for the collection of forensic evidence. If in doubt about a situation, for example concerning computer misuse, contact HR for advice.
Management responsibilities and appropriate procedures must be established to ensure an effective response against security events. The security advisors from HR must decide when events are classified as an incident and determine the most appropriate response.
An incident management process must be created and include details of:
The process must also include a section referring to the collection of any evidence that might be required for analysis as forensic evidence. The special procedure for preserving evidence must be carefully followed.
The actions required to recover from the security incident must be under formal control. Only identified and authorizedstaff should have access to the affected systems during the incident and all the remedial actions should be documented in as much detail as possible.
The officer responsible for an incident should risk assess the incident based on the Risk Impact. If the impact is deemed to be high or medium this should be reported immediately to Human Resources.
The following procedure will be followed for all security incidents in order to discover the root cause of the incident and to produce a final report.
Notification of the results of the issue that has been resolved should be provided by the Manager to the incident team, Owner of the company and the customer.
To learn from incidents and improve the response process incidents must be recorded and a post incident review conducted. The following details must be retained:
The information must be collected and reviewed on a regular basis by Human Resources and any patterns or trends identified. Any changes to the process made as a result of the Post Incident Review must be formally noted.
The information, where appropriate, should be shared with the warning, advice, and reporting point to aid the alert process for Northeast Data.
Note: Northeast Data reserves the right to modify this policy at any time.
Return Home